What is it?
Google offer a two step authentication system for their websites where, in order to log in, a user must enter both their password and a special number displayed on the user's phone using a special app that displays a changing unlock code. This code is only valid for a 2 minute window, and so a hacker needs access to the device as well as your password in order to log in.
An implementation behind this is also available in the form of a PAM module so you can install the same security on your PC. Despite being written by Google engineers, everything is run locally and it does not use your Google account.
As well as installing the PAM module you will want to download "Google-Authenticator" from the Android marketplace or iPhone store. Both of these are open source.
Installation & Usage
Install through your package manager
sudo apt-get install libpam-google-authenticator
or download the source
Once installed, run
google-authenticator
. You will be prompted with a series of questions, and then a secret key will be provided. Alternately scan the barcode into the phone to set everything up automatically.

|

|
|
Konsole output
|
How it appears on an Android phone
|
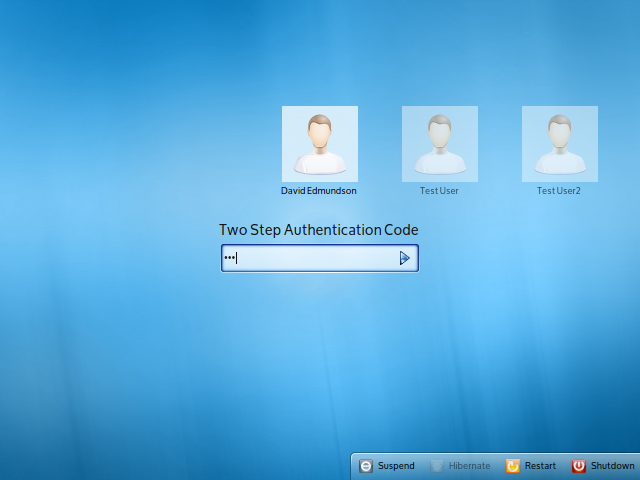
Integration in LightDM-KDE
I added support for this method in an experimental branch of lightdm-kde available at: git://anongit.kde.org/scratch/davidedmundson/lightdm-kde.git in the branch google-auth.
In order to use the two-step authentication we need to add the following line
auth required pam_google_authenticator.so
to one of the files in /etc/pam.d. Each file represents an authentication usage, and adding this line tells it we require google_authenticator to log in.
Add this line to /etc/pam.d/lightdm to force LightDM to prompt for the two-step verification code. It can be added to other files to prompt on console login or sudo for example, but note that it will not work in KDM.
The Future
PAM support in graphical prompts still needs a lot of work, this mostly stems from the fact that PAM was not really designed with graphical interfaces in mind.
Moving forward we need graphical interfaces to configure PAM, and GUI support for a range of modules, not just in LightDM-KDE but also in PolKit prompts, lock screens etc. I intend to kickstart this on the LightDM side, to support more PAM methods in a more elegant way and hopefully improve the existing kgreet library.