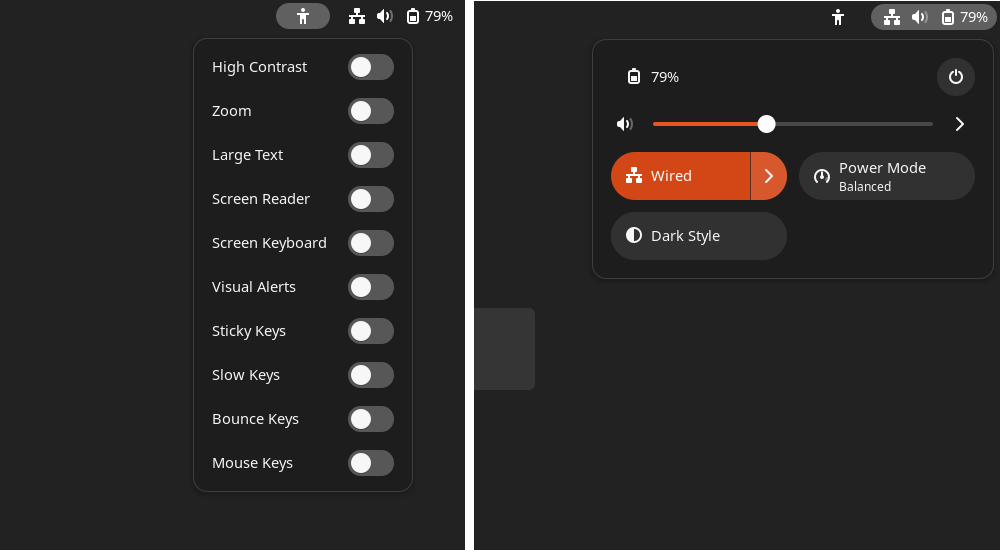
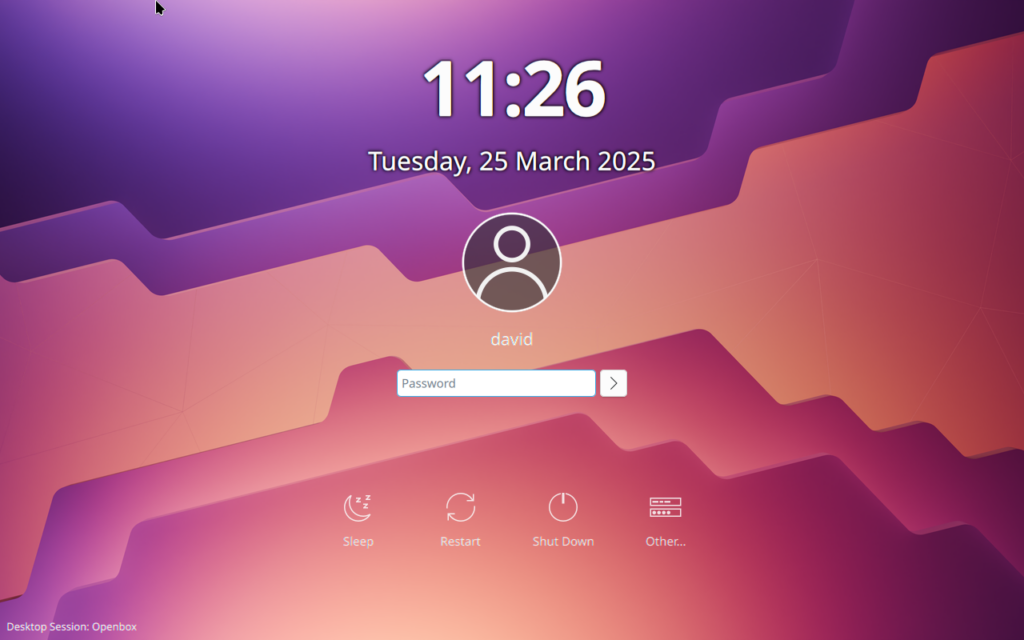
Plasma's login experience is an area that we know requires some improvement — it works OK in the basic case, but it's very barebones and doesn't handle anything beyond that.
As a complete desktop experience, it's our job to provide support for the edge cases too.
What we want
- Great out-of-box experience in multi-monitor and high DPI and HDR
- Keyboard layout switching
- Virtual keyboards
- Easy Chinese/Japanese/Korean/Vietnamese (CJK) input
- Display and keyboard brightness control
- Full power management
- Screen readers for blind people (which then means volume control)
- Pairing trusted bluetooth devices
- Login to known Wi-Fi for remote LDAP
- Remote (VNC/RDP) support from startup
A brief history
In Plasma 5, we retired our own bespoke display manager KDM, in favour of SDDM. A display manager started for multiple lightweight Qt Desktops. It was modern at the time making use of new QML for the front and as a big selling point at a time when Plasma was also making use of it.
SDDM's Big Architecture Problem
We ran into a problem, though. SDDM is designed to show a single greeter window, loading arbitrary QML from the specified theme.
Whilst this all sounded great for Plasma, the abstraction is at the wrong level — for our wishlist we need a lot more tight integration from our login screen than just a window showing sessions and users.
With SDDM, power management is reinvented from scratch with bespoke configuration. We can't integrate with Plasma's network management, power management, volume controls, or brightness controls without reinventing them in the desktop-agnostic backend.
SDDM was already having to duplicate too much functionality we have in KDE, which was very frustrating when we're left maintaining it.
The Competition
GNOME's GDM is the gold-standard of display managers, and it achieves this higher level of quality by running half of a Gnome session.
SDDM got closer when it added Wayland support — it had to use a compositor such as KWin. But because the project tries to be agnostic between desktops, it has to support any compositor. There aren't compositor-agnostic ways to do even simple things like set the keyboard layout, so in the end this compositor agnosticism goal simply didn't work.
Theme Problems
A major mistake we made throughout Plasma 5 was conflating "writing UI in a high level scripting language" with "it's themable" as the same thing — they are not. QML does make it easy to modify and iterate without programming skills, but it still contains business logic. It should not be the primary method of customisation that we expose to users.
Ultimately, this was poor for end users. We pushed back on adding support for configurable theme options, because building a theme engine within a theme was wasteful! But often people want to just change a few things. Choosing a theme meant finding a combination that had everything. The store filled up with themes that are 99.9% identical code-wise; most are just wallpaper mods.
It was also poor for theme developers. Not only do they have to modify the visuals, but also re-implement focus handling, accessibility, and the same boring logic again. They can't benefit from widespread testing so regressing these functionalities is common. Reddit is full of screenshots of broken SDDM themes.
Finally, it's poor for us Plasma developers: theme support holds us back from adding new features or tidying code; if we want to add a new feature that in any way affects existing UIs, the situation get very messy very fast. The end result is that features just don't land, and the end user is the one that misses out.
So, what's the plan?
It's worth stressing nothing is official or set in stone yet, whilst it has come up in previous Plasma online meetings and in the 2023 Akademy. I'm posting this whilst starting a more official discussion on the plasma-devel mailing list.
Oliver Beard and I have made a new mutli-process greeter, that uses the same startup mechanism as the desktop session. It doesn't have all the features that we propose at the start of the blog, but an architecture where features and services can be slowly and safely added.
For customisation we intend to expose the same familiar settings that exist in Plasma and bring the design more in-line with the existing screenlocker where we also dropped arbitrary QML years ago. We'll make the wallpaper configurable with any existing wallpaper plugins, and expose the existing plasma theme and colour settings. Syncing will be a case of copying files, not re-inventing things.
The backend
When starting work on this, I tried to explore all alternative backends out there even with fully working implementations, however in practice nothing was maintained that matched our requirements. SDDM has been proven in the real world, so we have taken that and stripped it down to cover what we want moving forwards. I also aim to incubate it into the KDE ecosystem to have full autonomy over the project and merging stuck patches.
Current State
All of this has been implemented as two new repositories. Plasma Login Manager a continuation of SDDM and Plasma Login for front end and KCM (settings) code. These might be merged at some point.
The new code all works, and is at roughly feature parity with what we're replacing. A screenshot looks roughly the same as a stock Plasma SDDM setup. Whilst this is at a state where developers can opt-in, I would not want distros to be packaging things at this point.
Please do reach out if this sounds interesting, either directly or in the Plasma Matrix room - or with merge requests!